IP cameras, Shodan and uPnP
You know it's bad when you can watch someones CCTV remotely without no authentication or whatsoever.
Case Presentation
Many people don't realize how exposed their devices, data and life is, whenever they connect to the internet. The internet is a product of historical events and technological breakthroughs in computer science and is a pinnacle for our efforts as a species. However, many of its protocols were not designed with security and privacy in mind, because in the baby days of the internet it was only used by a small circle of individuals, government agencies, researchers and military personnel.
This changed rapidly, with the increasing number of new internet-connected devices, for example personal computers and smart phones. There is, however a large group of devices, which most people tend to forget about, IoT (Internet of Thimgs) devices. IoT is an umbrella term, it includes every consumer and industry grade device which connects with each other via the internet. A research I found states that more than 19 billion devices are currently in use. These can range from your smart appliances, like your fridge or vacuum cleaner, to your IP camera, which you bought for the sake of security, but you might have just made your situtation worse, as you will see.
Some basics about computer networks
IP cameras are basically cameras which stream their video stream over the IP (Internet Protocol).
Computer networks work in a layer model, where each layer has a responsibility, interfaces to implement, and their implementations are not dependent on each other, as long as their interfaces stay the same. Like if you want to produce a light bulb, you don't really wanna care about how does the electricity gets to the power outlet, you live with the assumption that it's there, because another layer works out it somehow. If you want to learn more about this look into the OSI or the TCP/IP model.
Each layer implements protocols, protocols are set of rules of an action, like what, how, when, in what order should an action happen between computers. We humans also have protocols like:
- Look into the other person's eyes.
- Give our hands to each other.
- Grip the other hand and shake it.
- Say 'Good morning!'
- Release the hand.
- Walk away.
or
- Pour cereal into bowl.
- Pour milk into bowl.
- Eat.
In this exact order, if you put milk before cereal into the bowl, no worries this website is a 'kink shaming free' zone..
IP is a protocol which main responsibilty is for packets to get from device A to device B end-to-end, without a care if the packet gets corrupted, get lost or whatever. It's a best effort protocol. It's like the mailman who delivers the packets except the mail company doesn't care if the letter is damaged, or if the mailman stops because he is not paid enough (any similarity to actual events or individuals is the result of chance :))). You might have heard about IP addresses: these are the addresses the mailman uses to find the recipient's post box. Forgive me for not getting into too much details, but I don't want this to be too long (edit: i failed in this), and also want it to be understandable for the not so tech-savvy people.
IP addresses are important for us, since these addresses are our identifiers on the plains of the cyber world. IP addresses can be IPv4 or IPv6. IPv4 addresses are in the format of A.B.C.D where A, B, C and D are 8 bit integers, so decimals ranging from 0 to 255. So the address space is 32 bit, which gives us around 4.3 billion unique addresses, I think you can already see whats the problem with this...
Computer scientists realized in the 90's that this address space is gonna be exhausted pretty soon with appearance of new, widely used computers. They came up with the idea of CIDR and NAT, which made it possible to use public and private addresses. So basically, sticking with our analogy, a public address is what the mailman uses to deliver your package to the housing complex you live in, but he doesn’t know which room to deliver it to. The private addresses are used locally and are not routable on the internet, these are the room number the mailman couldn't know, the doorman (the firewall on your router) would only let the mailman in if the communication was initiated from inside.
This gives you the very foundational knowledge to understand how a standard home network works: a router which was given to you by your ISP is connected to the internet and is given a public IP address, and this router manages your network, gives out private addresses inside the home network, and whenever you want to communicate with the outside world, this router translates your private IP address with NAT, to its public address.
This was the first proposed solution to IP exhaustion, since now not every device has to be given a unique public address, rather addresses from the private address (like from the 192.168.0.0/16 range) can be used. However this was not considered a long term solution, so they came up with the idea of IPv6 addresses, but we are not going into that rabbit hole...
The main reason I wanted this to be explained, because now port forwarding will make sense. So first let's talk about ports: ports on your computer, are like windows or doors on your house (which now the mailman can find :DD). From a security point of view, you would want those doors and windows locked, don't you? In layman terms, port are used by services to communicate on the network. An address:port combo unambigously identifies a service. Like when you host a Minecraft server, you open a port on your computer where the Minecraft server service can listen on, and your friends can talk to that port and join your game. If your computer was given a private IP address these services are only accessible from your local network, as I explained previously. Many use cases (like the Minecraft server) require to make these services exposed to the internet so others can use it or reach it. Like if you are running a website from your own server. This is where port forwarding comes into play, it basically is what is says: your router will forward every packet coming to its X port to a host's X port inside its network. So a Minecraft server would be reachable on the router's public address, on the port 25565. This is useful if you know what you are doing, but it can end horribly if you are not cautious. This is because with port forwaring you make your service behind that port accessible to the whole world, and belive me there are thousand of bots who bang their heads every day at your "door" trying to break in. AT LAST we are getting close to the main point of this blog post.
The patient
So I knew long before now, that many people are not really aware sometimes what they do, and they expose things which shouldn't be exposed. Only if I knew how bad things were. Not so long ago I started to play with shodan.io which is very useful for security researchers or enthusiasts like me. You can query this website with different parameters, and in response it will give you the hosts which fulfilled the query. The curiosity killed the cat, and I searched for many things, like IP cameras in Hungary. This is where the stuff I yapped about in the previous paragraphs starts to matter.
Discovery
Quoting from the Shodan's website:
Shodan is the world's first search engine for Internet-connected devices. Discover how Internet intelligence can help you make better decisions. Keep track of all your devices that are directly accessible from the Internet. Shodan provides a comprehensive view of all exposed services to help you stay secure.
Shodan only scans the internet for:
-
Which IPs respond on certain ports
-
What banners/services they expose (e.g., HTTP headers, RTSP response codes, SSH version strings, etc.)
This is how it looks when you search for something:
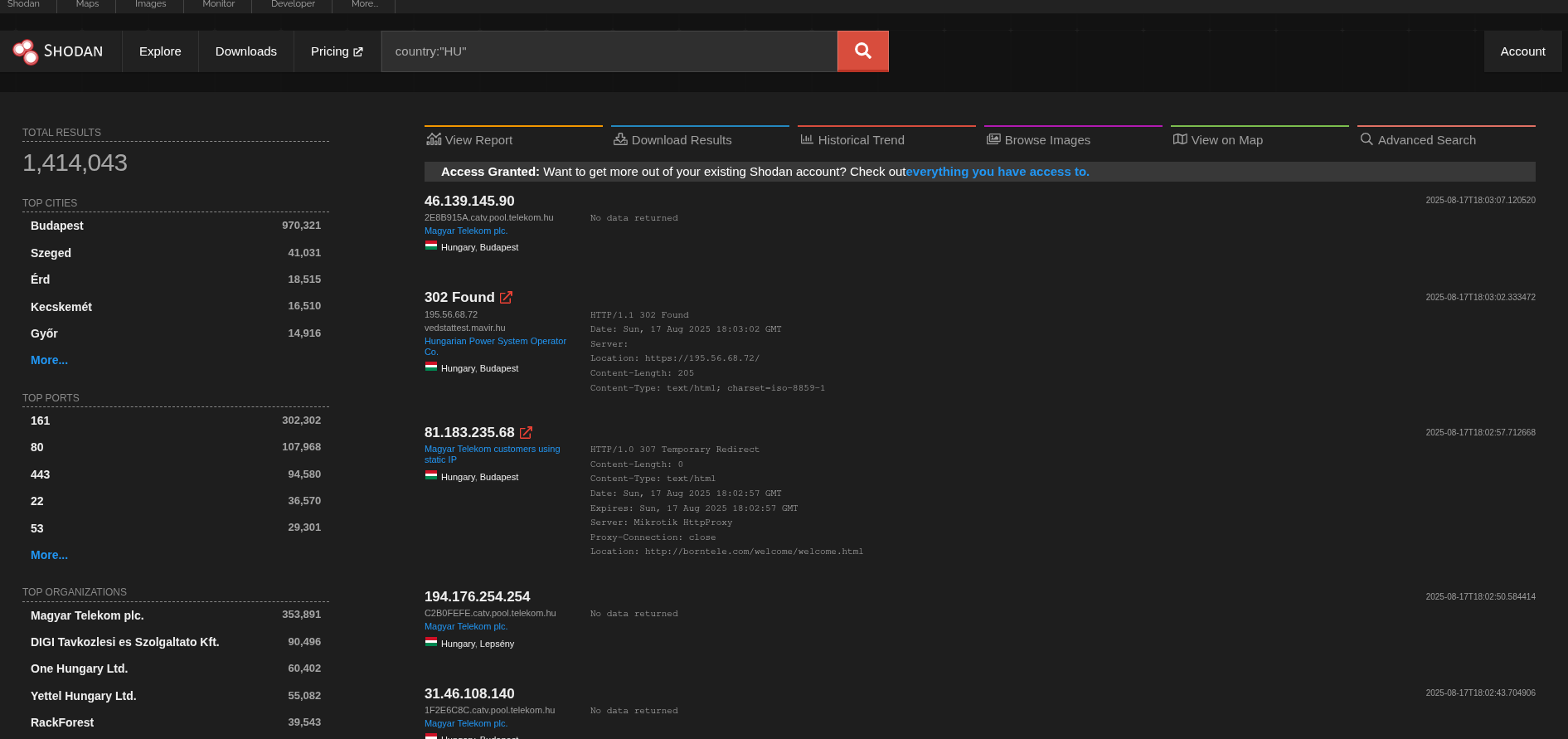
So with this tool, anyone and I mean anyone, can look at what ports, services are running on a public IP address. Also this works in the other way around, you can look for IP addresses which serves something you are interested in. As you can see in the example, I just searched for country:"HU" so everything which is in Hungary. Shodan API can give you access to a programmable interface to automate this process of searching. Important to note that with Shodan I don't actively port scan, Shodan does that for me periodically, I just query the database.
Now I can search for ports and services I'm specifically interested in.
Illness
I will cut it short, you can basically search for cameras on Shodan which are somehow exposed to the public. This is very bad, if it's not intentional (like weather live feeds). Imagine you install a camera so you feel more secure, but now someone on the other side of the world can watch the same feed.
To give you a presentation of this:
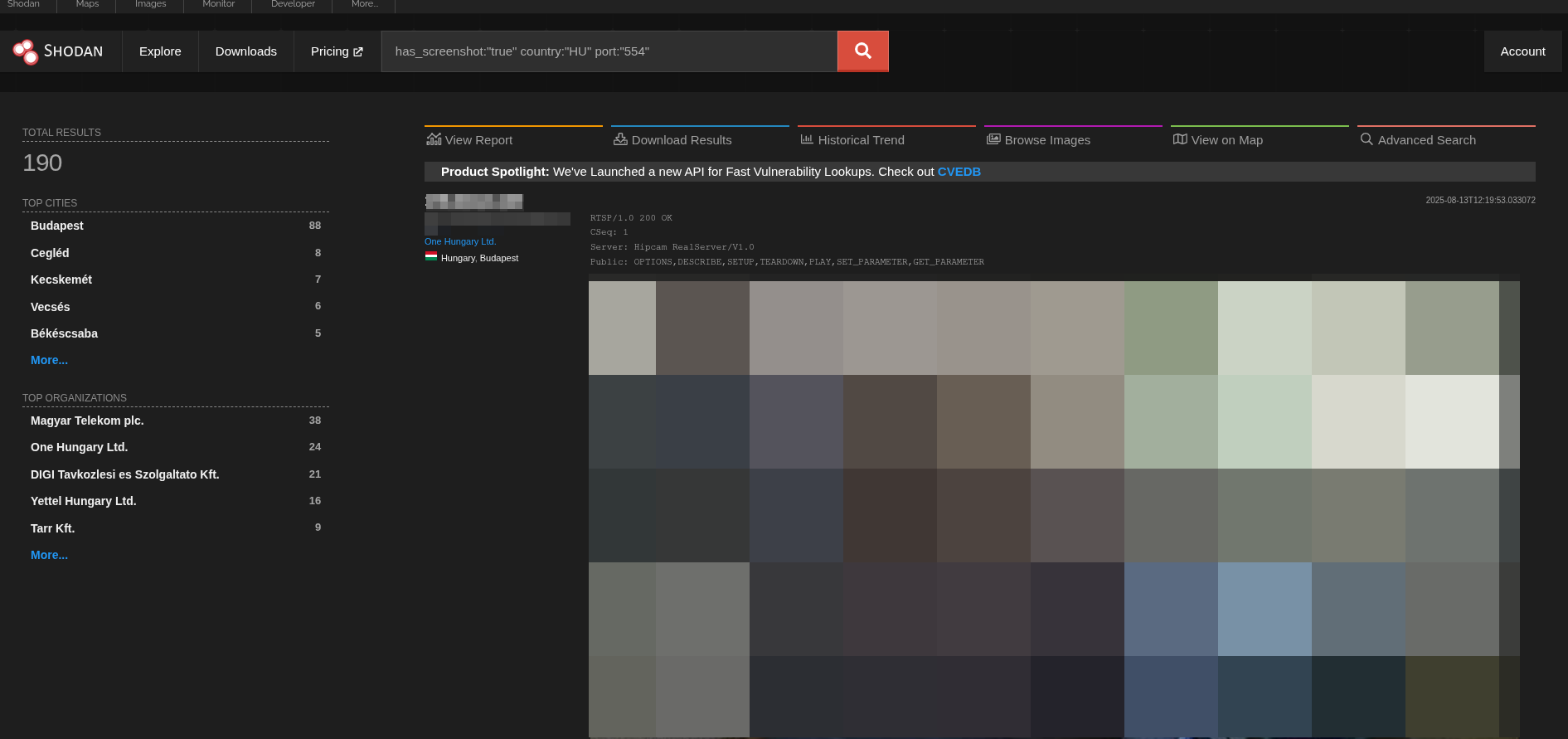
I blurred out the actual image and IP of the host, not like you couldn't find out of the 190 results you find like this, but this felt like the right thing to do.
The query: has_screenshot:"true" country:"HU" port:"554"
What I did here:
- has_screenshot:"true" - it will filter to hosts where Shodan was able to get a screenshot, in the context of cameras, it means that Shodan could connect to it with default credentials, or without any authentication,
- country:"HU" - makes it so I only see hosts from Hungary,
- port:"554" - filters down to hosts where the port 554 responded, 554 port is the default port for RTSP (Real Time Streaming Protocol), which is basically the same as the remote control for your TV, just in terms of IP cameras
As you can see there are around 190 cameras in Hungary which are open like this, and god knows how many more I would find with refining the query.
This is only the tip of the iceberg, since there are thousand other ports, services I could have searched for. I chose cameras because they are very representative since its very much visual.
Diagnosis
I came up with 2 reasons why someone could expose their camera like this:
- Out of carelessness, manually port forwarding the 554 port to see the camera, even when you are not at home.
- uPnP: Universal Plug and Play was invented so people doesn't need to configure IoT and networkable devices, the devices can discover, describe and control each other automatically, and when a router has uPnP enabled, other uPnp devices can request port forwards on the fly. So people plug in their camera and implicitly, their camera talks with their uPnP enabled router and talks down a port forward, without the owner explicitly setting this.
I would like to elaborate the second one a bit more. uPnP is not secure by design, it does not require devices to authenticate themselfs, and can also hide configuration, like in the example above, which may not have been intended. Also if a device in your network get infected with a malware then it could lead to lateral movement or other malicious activtiy on your network, because that infected device could use uPnP to control other devices. This could potenltionally lead to punching a hole in your firewall if your router has uPnP. Unforutnately, many routers come with uPnP enabled by default :((.
Treatment
To finish this long ass post, I want to give some remedies and mitigations, not only for securing your IP cameras, but in general:
First of all, you should always strive for solutions, which do not requires you to open up ports on your router with port forwarding. For example if you have a CCTV, and you want to reach it remotely, you can always setup a VPN, forward a port to the VPN server, and use that to reach the feed, it's not that hard. A VPN is not just remote access, it's a remote access where the CIA (Confidentiality Integrity Availability) requirements are met. VPN creates a secure encrypted tunnel, between you and your network, so nobody can eavesdrop on your packets, while it travels from your end devices. A simple RTSP stream will be unencrypted. If you don't know and don't want to setup a VPN, and don't have anyone who could help with it, you could always resort to buying an IP camera which has a vendor cloud server, which completely solves the open port issue, however you will have to trust the vendor that it's not gonna look into your feed at its server, which is still bad in my opinion. You shouldn't settle for solution which requires a "trust me bro" type of relationship between you and the vendor. Especially when you find it that most of the vendor servers are in China...:)). If you really, really cannot avoid opening up ports, you should always expose as minimal as possible, and with maximum care. Put authentication before it, which cannot be brute-forced, since many bots will try to break it, using password wordlists, and fuzzing.
Second of all, do not use uPnP, that's it.
Is this legal?
Yes, I'm sure the question "Wait this guy is actually looking at random camera feeds?" came to your mind.
The answer to that question is no.
This gets into where Shodan and I stop, and where does the law start.
Querying Shodan is completely legal, also what Shodan is doing is also legal because:
No hacking/exploitation: Shodan does not use vulnerabilities, buffer overflows, or brute-forcing. It only asks: “If I connect normally, what do you give me?”
Public exposure: The camera owners (or their routers via UPnP) have placed the stream on the open internet. Legally, that’s closer to “broadcasting” than “private access.”
Precedent: Courts and researchers often compare this to a web crawler — like Google indexing publicly available web pages. If you didn’t put up authentication, the bot is just recording what’s already public.
The grey area starts when you actively watch real time camera feeds, and interact with them, which is clearly not meant to be public and could cross the line of unauthorized access.
However just taking a screenshot is not illegal. Analogy for this: when you don't close the blinds on you windows and a passerby takes a glimpse, obviously if the passerby would watch you from you window continously, it would mean the invasion of privacy.
Exploiting a vulnerability in an exposed port, is considered a serious crime so don't do it. Just because a door is open, doesn't mean you were given access to enter it. It's not a game.